Cybersecurity Built for Real Businesses, Not Tech Departments
Protect your business, your reputation, and your team with clarity, not complexity

Why Most Cybersecurity Services Confuse, Not Protect
“They speak in jargon. They charge for extras. And they still leave you guessing what’s actually covered.”
QuantumCare changes that. It's built for business owners—not IT pros. It’s the all-in-one protection package designed to simplify, secure, and support your business without hidden gaps.
What You Get
What You Get
Complete cybersecurity coverage that protects every aspect of your business—from users to servers to strategic guidance.
User Security
Protect your people and their accounts
- Account protection with multi-factor authentication
- Dark Web monitoring for compromised credentials
- Regular Security Awareness Training
- Realistic Phishing Tests to build awareness
- Password policy enforcement and monitoring
Device Security
Every laptop and desktop fully protected
- Advanced endpoint protection on all devices
- System hardening to close security gaps
- 24/7 continuous monitoring and threat detection
- Automatic malware removal and quarantine
- Device compliance and configuration management
Server Security
Complete server protection and maintenance
- Full server protection and hardening
- Automated patching routines with testing
- Server performance and security monitoring
- Backup verification and disaster recovery planning
- Access control and privilege management
Network Security
Fortress-level network protection
- Professional firewall configuration and management
- Regular network security auditing
- Ongoing firewall rule optimization
- Network traffic monitoring and analysis
- Intrusion detection and prevention systems
Microsoft 365 Security
Cloud productivity, securely configured
- Complete cloud security hardening
- Automated daily backups of all data
- SPF, DKIM, and DMARC email authentication setup
- Advanced threat protection configuration
- Data loss prevention and compliance settings
Attack Surface Scanning
Find vulnerabilities before hackers do
- Regular hacker-style vulnerability scans
- External and internal network assessments
- Web application security testing
- Social engineering and phishing assessments
- Detailed reports with actionable remediation steps
Incident Response
Expert help when you need it most
- 24/7 emergency incident response
- Rapid threat containment and isolation
- Digital forensics and root cause analysis
- Recovery planning and system restoration
- Post-incident reporting and improvement recommendations
vCISO Access
Strategic security leadership without the salary
- Strategic cybersecurity planning and roadmaps
- Board-level security reporting and presentations
- Compliance and regulatory guidance
- Security budget planning and vendor evaluations
- Executive security awareness and training
Security Policies
Bespoke documentation for real compliance
- Custom security policies tailored to your business
- Compliance frameworks (ISO 27001, GDPR, etc.)
- Employee security handbooks and procedures
- Incident response playbooks
- Regular policy reviews and updates
Data Destruction Guidance
Secure and compliant disposal processes
- Secure data wiping and destruction protocols
- Compliance with data protection regulations
- Certificate of destruction documentation
- Physical device disposal coordination
- End-of-life equipment security guidance
Ongoing Risk Reviews
Stay ahead of threats, don't react to them
- Quarterly comprehensive risk assessments
- Threat intelligence monitoring and analysis
- Security posture scoring and improvement tracking
- Industry-specific threat briefings
- Proactive security improvement recommendations
The Framework We Follow to Deliver the Service
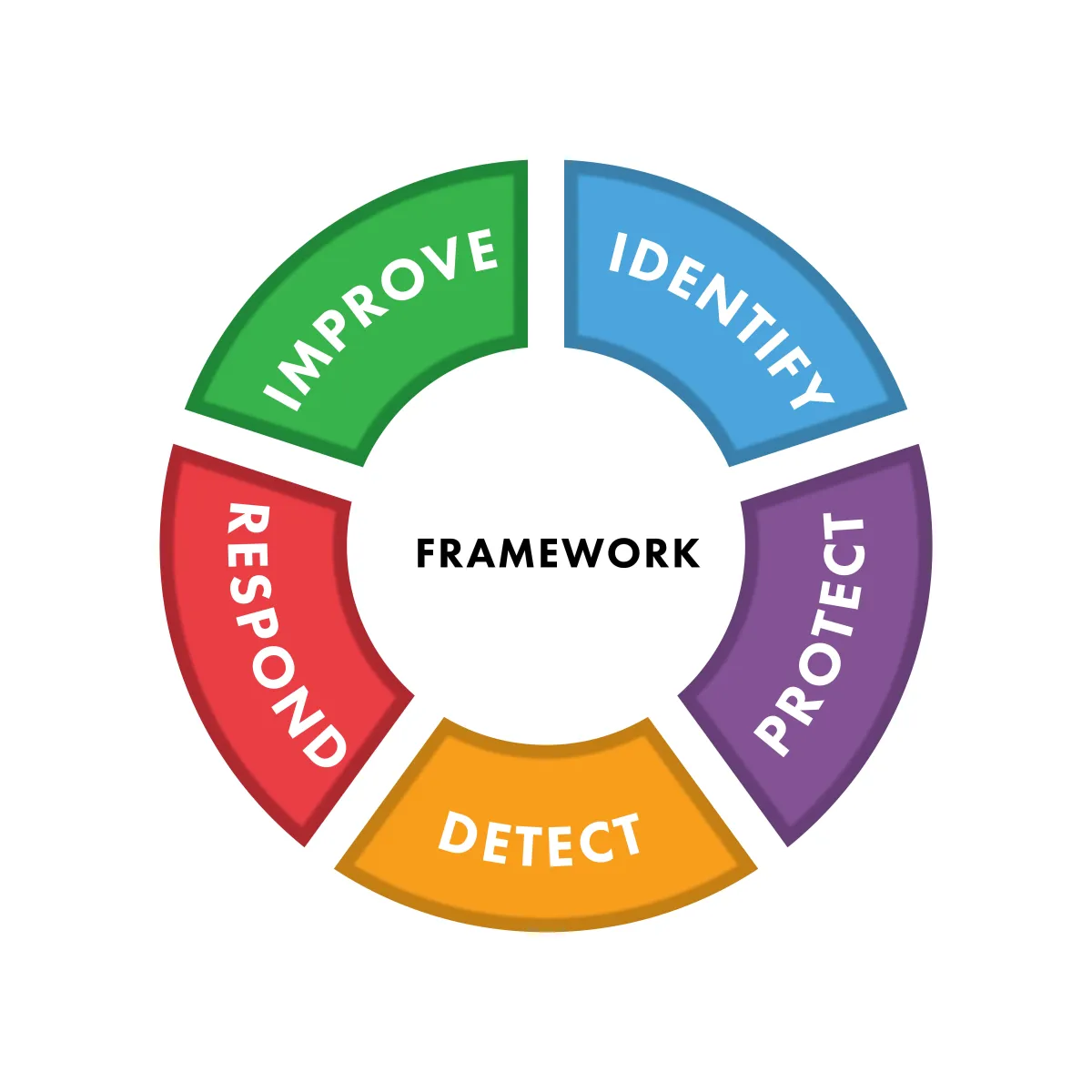

Is This You?
QuantumCare is purpose-built for growing businesses that know cybersecurity isn’t optional — it’s critical.
It's a great fit for organisations with 10 to 250 employees, £1M+ in annual turnover, and existing internal or outsourced IT support. If you’re serious about protecting your business, your clients, and your reputation, QuantumCare gives you a dedicated cybersecurity partner that feels like part of your team.
Prefer remote-first delivery, clear priorities, and ongoing expert guidance — not just a one-off fix?
You're exactly who we built this for.
When can I use my Pre-Purchased Hours?
Pre-purchased hours are available Monday to Friday, 9:00 AM to 5:00 PM (UK time), excluding UK bank holidays.
Need out-of-hours support? Click Schedule Call to talk through options.
Do the hours cover on-site work?
No. Ad-hoc hours are for remote work only. If you need us to come on-site, click Schedule Call and we’ll talk it through — location, scope, and cost.
Are your services delivered remotely or in-person?
Most services are delivered remotely. It’s faster, more secure, and more cost-efficient. If you prefer on-site help, just hit Schedule Call and we’ll arrange what works for you.
Do unused hours expire?
es — pre-purchased hours are valid for 90 days from the date of purchase. This helps us manage engineer availability and deliver reliable support.
That said, we aim to be as flexible as possible. If you're approaching the deadline and need more time, just get in touch — we’ll do our best to accommodate.
Can I split the hours across multiple jobs?
Absolutely. Use your hours across different requests, departments, or teams. Just make sure they’re used within the 90-day window.
What kind of tasks can I use ad-hoc hours for?
Popular uses include:
- System Hardening / Configuration
- Email/phishing analysis
- Firewall or router config
- Microsoft 365 hardening
- Cyber Essentials pre-audit fixes
- One-off vulnerability scans
- Employee security training setup
- Incident response or investigation
If you're unsure, reach out.
What happens if I run out of hours mid-task?
We’ll pause and notify you before continuing. You’ll have the option to top up hours so we can complete the work.
Is there a refund if I don’t use all the hours?
No. These hours reserve expert time in our calendar. They’re non-refundable — but you can maximise value by bundling smaller jobs or using them for proactive checks or improvements.

Innovation
Fresh, creative solutions.

Integrity
Honesty and transparency.

Excellence
Top-notch services.

FOLLOW US
Systems Secure Ltd
6 The Meadow, Copthorne, West Sussex. RH10 3RG
07588 455611
Company Registration: 7295869
COMPANY
CUSTOMER CARE
LEGAL
Copyright 2025. Systems Secure. All Rights Reserved.
